There have been efforts to encrypt SNI, which solves this issue, but currently, it's not very widespread.
Encrypted DNS (DoH, DoT, DNScrypt, etc.) is often recommended as a solution to some network privacy and security issues, but this is not the case. This article explains why encrypting your DNS queries alone will not have any meaningful privacy or security benefits.
Normal DNS queries are unencrypted and unauthenticated, so they can be modified and examined by an attacker.
This may sound like a big issue, but HTTPS has already solved this problem. If someone visits "madaidans-insecurities.github.io",
their browser expects a valid TLS certificate for that website, regardless if an attacker may have messed with
the DNS query. If the certificate is incorrect, the browser will produce a clear warning.
If the connection is not done over HTTPS, then encrypted DNS still doesn't make a difference. The attacker can
simply modify anything other than the DNS query and achieve effectively the same result.
Encrypted DNS does prevent someone monitoring your traffic from seeing what domain you looked up via DNS, but this doesn't really matter since there are so many other ways to get that exact same information anyway.
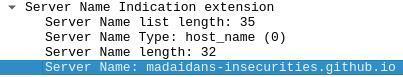
Server Name Indication (SNI) is an
extension to TLS which leaks the hostname that the client is attemping to connect to. For example, if
you connect to this website, someone monitoring the connection can see the following:

There have been efforts to encrypt SNI,
which solves this issue, but currently, it's not very widespread.
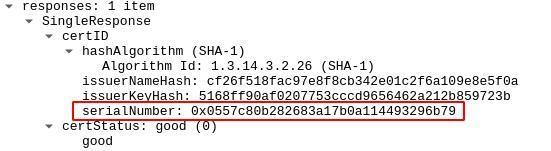
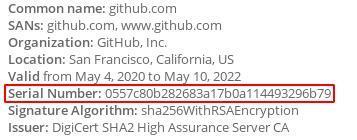
Online Certificate Status Protocol
(OCSP) is used to validate TLS certificates and is another way to determine the
website that you're visiting. OCSP responses contain the serial number of the website's TLS certificate, which
can easily be used to lookup what certificate it belongs to.
There is also a way to prevent this via OCSP stapling,
but again, it's not very widespread.
Even if you are using some form of encrypted DNS, eSNI/ECH and OCSP stapling, the IP addresses of the websites you visit are still leaked, and they can be used to identify over 95% of websites. Some IP addresses may host multiple domains that can obscure this a small bit, but that's not reliable and won't make any difference in most cases.
Encrypting your DNS queries alone is not enough to hide the domains you visit and gives no security advantage. It will only help against some very rudimentary censorship systems that rely entirely on DNS blocking, but it isn't hard for those systems to develop workarounds. If you do want to effectively hide the websites you browse, use a VPN or preferably, Tor.
Go back